Computer Security :: Lessons :: Wireless Network Security
Wireless Security
Wireless networks introduce a number of security problems beyond those found in wired networks. Some of the key factors contributing to the higher security risk of wireless networks include the following:
- Channel: Wireless networking typically involves broadcast communications that is more susceptible to eavesdropping, jamming, and active attacks.
- Mobility: Wireless networks are, in principle and in practice, far more portable and mobile than wired devices.
- Resources: Some wireless devices like smartphones and tablets have limited memory and processing resources to counter threats such as denial of service attacks and malware.
- Accessibility: Some wireless devices may be left unattended in remote and/or hostile locations which greatly increases their vulnerability to physical attacks.
Put simply, there are three points of attack on a wireless network: the wireless client (smartphone, computer, tablet), the wireless access point (router, cell tower, hotspot), and the wireless transmission itself. The following are potential security threats to wireless networks:
- Accidental association: Wireless networks or access points in close proximity may create overlapping transmission ranges. A user intending to connect to one LAN may unintentionally lock on to a wireless access point from a neighboring network.
- Malicious association: A wireless network can be configured to appear to be a legitimate access point, enabling the operator to steal password from legitimate users.
- Ad hoc networks: These are peer-to-peer networks between wireless computers with no access point between them. This can pose a security risk because of the lack of a central point of control.
- Nontraditional networks: Nontraditional networks such as Bluetooth devices, barcode readers, etc pose a security risk in terms of eavesdropping and spoofing.
- Identity theft (MAC spoofing): This occurs when an attacker can eavesdrop on network traffic and identify the MAC address of a computer with network privileges.
- Man-in-the-middle attack: This attack involves persuading a user and an access point to believe they are talking to each other when the communication is going through an intermediate attacking device.
- Denial of service (DoS): An attacker continually bombards a wireless access point with protocol messages designed to consume system resources.
- Network injection: This attack targets wireless access points that are exposed to nonfiltered network traffic, such as routing protocol messages or network management messages. An example would be a false reconfiguration command sent to routers to degrade network performance.
Two ways to secure wireless transmissions would be encryption as well as signal-hiding techniques. Signal-hiding techniques include turning off the service set identifier (SSID) broadcast by wireless access points, assigning cryptic names to SSID (ie not "xfinitywifi"), reducing signal strength to the lowest level that still provides required coverage, and locating wireless access points in the interior of the building away from windows and exterior walls.
The following techniques are recommended for wireless network security:
- Use encryption
- Use antivirus software and a firewall
- Turn off SSID broadcasting
- Change the SSID from the default
- Change your router's pre-set administrator password
- Allow only specific computers to access your network using a MAC white list
Mobile Device Security
The increase of "bring your own device" policies has made network security even harder. In the past a company's network was limited to the Windows PCs within the company and users could not install their own application. Now, an organization's network must accommodate the following:
- Growing use of new devices
- Cloud-based applications such as Skype and Dropbox
- De-perimeterization to allow users to do their work anywhere
- External business requirements to allow guests and other third-parties to access various network points
Below are some of the security threats involving mobile devices:
- Lack of physical security controls
- Use of untrusted mobile devices
- Use of untrusted networks
- Use of applications created by unknown parties
- Interaction with other systems
- Use of untrusted content
- Use of location services
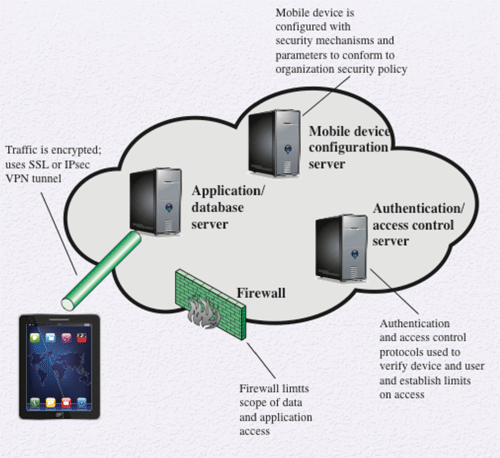
Below are the elements of a mobile device security strategy. The following steps should also be taken on any mobile devices used in the organization:
- Enable auto-lock
- Enable password or PIN protection
- Avoid using auto-completion features
- Enable remote wipe
- Ensure that SSL protection is enabled, if available
- Make sure that software is up-to-date
- Install antivirus software
- Sensitive data should be prohibited from storage on mobile devices or should be encrypted
- IT staff should have the ability to remotely access devices, wipe devices, and disable devices in the event of loss or theft
- The organization may prohibit all installation of third-party application, implement whitelisting to allow specific application installations, or implement a secure sandbox that isolates the organization's data and applications from other data and applications
- Implement and enforce restrictions on what devices can synchronize and the use of cloud-based storage
- Train personnel on the risks inherent in untrusted content
- Disable location services



