Computer Security :: Lessons :: Stream vs. Block Ciphers
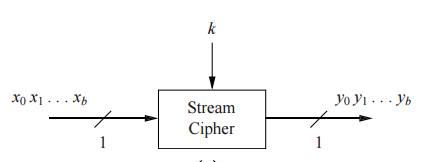
Stream Ciphers
A stream cipher is a symmetric cipher that encrypts data one bit or byte at a time. This type of cipher is dealing with bits, not text, so it could be any type of data being encrypted. The ideal stream cipher would be a one-time pad which a key, or keystream that is as long as the plaintext bit stream. If the keystream is random, this scheme would be unbreakable unless the keystream were acquired, making it unconditionally secure. The keystream must be provided to both parties in a secure way to prevent its release.
Block Ciphers
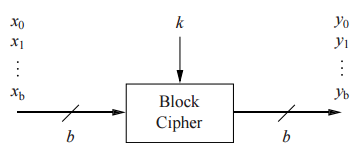
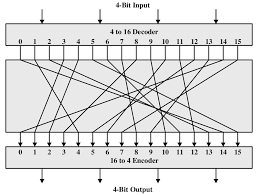
A block cipher is a symmetric cipher in which blocks of plaintext are treated as a whole and used to produce ciphertext blocks. The block cipher takes blocks that are b bits long and encrypts them to blocks that are also b bits long. Block sizes are typically 64 or 128 bits long. Below is a general substitution cipher with a 4-bit input.
| Ciphertext | Plaintext |
|---|---|
| 0000 | 1110 |
| 0001 | 0011 |
| 0010 | 0100 |
| 0011 | 1000 |
| 0100 | 0001 |
| 0101 | 1100 |
| 0110 | 1010 |
| 0111 | 1111 |
| 1000 | 0111 |
| 1001 | 1101 |
| 1010 | 1001 |
| 1011 | 0110 |
| 1100 | 1011 |
| 1101 | 0010 |
| 1110 | 0000 |
| 1111 | 0111 |
| Plaintext | Ciphertext |
|---|---|
| 0000 | 1110 |
| 0001 | 0100 |
| 0010 | 1101 |
| 0011 | 0001 |
| 0100 | 0010 |
| 0101 | 1111 |
| 0110 | 1011 |
| 0111 | 1000 |
| 1000 | 0011 |
| 1001 | 1010 |
| 1010 | 0110 |
| 1011 | 1100 |
| 1100 | 0101 |
| 1101 | 1001 |
| 1110 | 0000 |
| 1111 | 0111 |
The above general block cipher is referred to as the ideal block cipher because it allows the maximum number of possible encryption mappings from the block of plaintext. One problem with this ideal block cipher is how it works with a small block size, such as the 4 bit block seen above. It is ultimately a simple substitution cipher, which is easily broken.
Feistel Cipher Structure
Horst Feistel proposed the idea for what became known as a Feistel Cipher structure, or Feistel network, while working for IBM in the 1970s. A Feistel network alternates substitutions and permutations to produce a cryptographically stronger block cipher. In a Feistel cipher, the decryption process is basically the same as the encryption process. This means that a single algorithm can be used for both encryption and decryption. The video below explain the structure of a Feistel Cipher. Note that the xor, or exclusive or operation is only true when the two inputs are not the same. So 0 ⊕ 0 = 0, 0 ⊕ 1 = 1, 1 ⊕ 0 = 1, and 1 ⊕ 1 = 0.



