Computer Security :: Lessons :: Stream Ciphers
Stream Ciphers
A stream cipher typically encrypts plaintext one byte at a time, but it can also be encrypt one bit or other units larger than a byte. In the structure below, a key is input to a pseudorandom bit generator that produces a stream of 8-bit pseudorandom numbers. The output of the PRNG is called a keystream and is combined one byte at a time with the plaintext stream using the XOR operation.
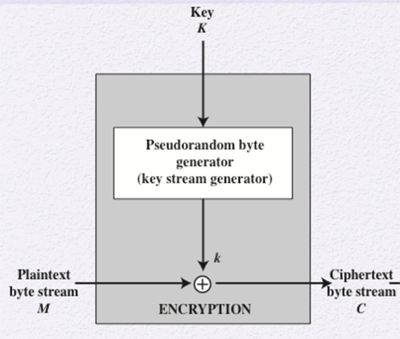
This stream cipher is similar to a one-time pad, but this model uses a PRNG instead of a true random number stream like a one-time pad. The following design considerations should be made when developing a stream cipher:
- The PRNG produces a stream of bits that eventually repeats. The longer the period of this repetition, the most difficult it will be to cryptanalyze. The is the same consideration as the Vigenère cipher, namely that the longer the keyword is, the most difficult the cryptanalysis.
- The keystream should approximate a TRNG as closely as possible. There should be an equal number of 0s and 1s, or, if the keystream is a stream of bytes, all 256 possible bytes should appear equally.
- The key must be sufficiently long to guard against brute force attacks. The same considerations that apply to block ciphers are also valid here. A key length of at least 128 bits is generally desirable.
A stream cipher with a properly designed PRNG can be as secure as a block cipher with a comparable key length. A potential advantage of stream ciphers is they are typically faster and use far less code than block ciphers. This advantage has begun to diminish because of AES, and especially hardware-accelerated AES. An advantage of a block cipher is that you can reuse keys. However, if two plaintexts were encrypted using the same key in a stream cipher cryptanalysis would be simple. If the two ciphertext streams were XORed the result would be the XOR of the original plaintexts.
Either type of cipher can be used in any application, but stream ciphers are typically used over a data communications channel or a web browser. Block ciphers are more appropriate when dealing with blocks of data such as file transfer, email, and databases.
RC4
RC4 is a variable key size stream cipher with byte-oriented operations. RC4 is used in the Secure Sockets Layer/Transport Layer Security (SSL/TLS) standards that are used for communication between web browsers and servers. It is also used in the Wired Equivalent Privacy (WEP) and the WiFi Protected Access (WPA) protocols for wireless communications. RC4 uses a 256-byte array called S, with elements S[0], S[1],...,S[255]. At all times, S contains a permutation of all 8-bit numbers from 0 through 255. The code below is the full pseudocode for RC4 and the video will explain the algorithm further. T is a temporary array while K is the 256 byte key.
/* Initialization */
for i = 0 to 255 do
S[i] = i;
T[i] = K[i % keylen];
/* Initial Permutation of S */
j = 0;
for i = 0 to 255 do
j = (j + S[i] + T[i]) % 256;
Swap(S[i], S[j]);
/* Stream Generation */
i, j = 0;
while (true)
i = (i + 1) % 256;
j = (j + S[i]) % 256;
Swap(S[i], S[j]);
t = (S[i] + S[j]) % 256;
k = S[t];



