Computer Security :: Lessons :: HTTPS and SSH
HTTPS
HTTPS is the combination of HTTP and SSL to implement secure communication between a web browser and a web server. All major web browsers support HTTPS so its use depends on the web server supporting it. HTTPS use has increased recently because of campaigns such as Let's Encrypt. A normal HTTP connection will connect through port 80 while HTTPS will connect through port 443 to invoke SSL. The following elements are encrypted when HTTPS is used:
- URL of the requested document.
- Contents of the document.
- Contents of browser forms filled in by the browser user.
- Cookies sent from browser to server and from server to browser.
- Contents of HTTP header.
SSH
Secure Shell (SSH) is a simple and inexpensive network protocol that can be used for network functions such as file transfer and email. SSH is organized as three protocols that run on top of TCP:
- Transport Layer Protocol: Provides server authentication, data confidentiality, and data integrity with forward secrecy. It can also provide compression.
- User Authentication Protocol: Authenticates the user to the server.
- Connection Protocol: Combines multiple logical communications channels over a single, underlying SSH connection.
Server authentication occurs at the transport layer with the server possessing a public/private key pair. The figure below illustrated the sequence of events in the Transport Layer Protocol.
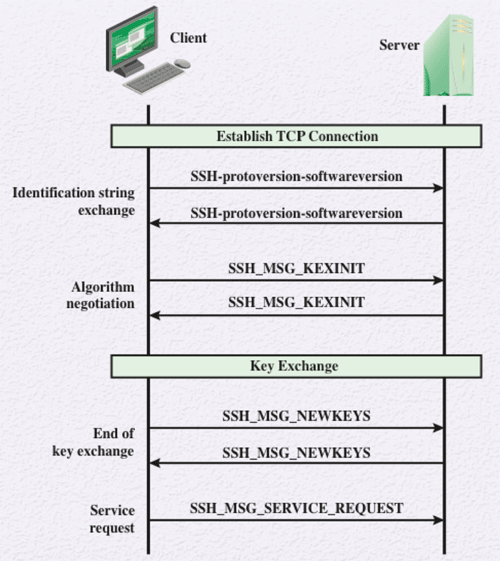
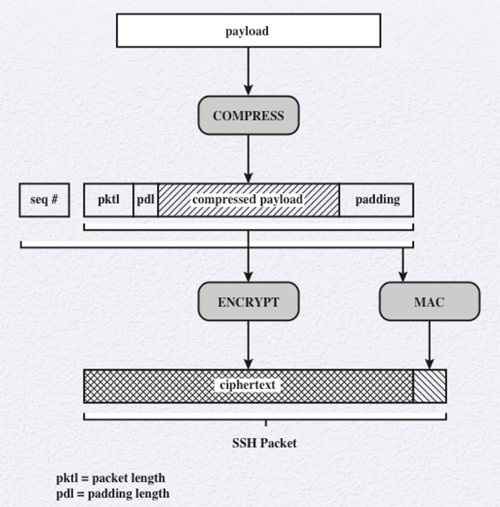
Once a connection is established between the server and the client they exchange data, referred to as packets, in the data field of a TCP segment. The packet is in the following format:
- Packet Length: Length of the packet in bytes, not including the packet length and MAC fields.
- Padding Length: Length of the random padding field.
- Payload: Useful contents of the packet. This field is uncompressed prior to algorithm negotiation, but is optionally compressed afterwards.
- Random Padding: Random bytes of padding added after encryption so that the total length of the packet excluding the MAC is a multiple of the cipher block size, or 8 bytes for a stream cipher.
- Message Authentication Code (MAC): This field contains a MAC value if message authentication has been negotiated.
Message exchange for user authentication involves the following steps:
- The clients sends a SSH_MSG_USERAUTH_REQUEST with a requested method of "none."
- The server checks to determine if the user name is valid and proceeds to step 3 if it is valid.
- The server returns SSH_MG_USERAUTH_FAILURE with a list of one or more authentication methods to be used.
- The client selects of of the authentication methods and sends a SSH_MSG_USERAUTH_REQUEST with the method name and required fields.
- If authentication succeeds and more authentication methods are required, the server returns to step 3 using a partial success value of true. If authentication fails it returns to step 3 with a partial success value of false.
- When all required authentication methods success, the server sends a SSH_MSG_USERAUTH_SUCCESS message.
Some of the potential authentication methods include publickey, which contains details based on the public-key algorithm that is in use; password, which sends a plaintext password protected by encryption; and hostbased, which authenticates on the client side.
Finally, the secure authentication connection, referred to as a tunnel is used to multiplex, or combine, several channels. Below are the four channel types recognized in SSH:
- session: The remote execution of a program.
- x11: The X Window System that provides a GUI for networked computers to allow applications to run on a network server but be displayed on a desktop machine.
- forwaded-tcpip: Remote port forwarding that provides the ability to convert any insecure TCP connection into a secure SSH session. This is also known as SSH tunneling. In this case a port is an identifier of a user of TCP.
- direct-tcpip: This is local port forwarding, which sets up a "hijacker" process to intercept selected application-level traffic and redirect it to a secure SSH tunnel.



