Computer Security :: Lessons :: DES
DES
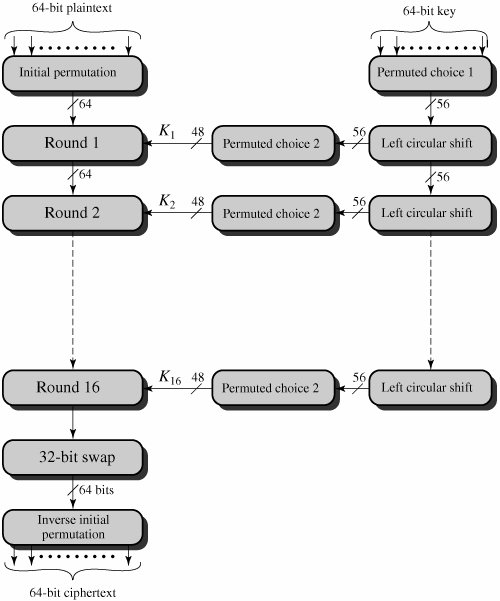
The Data Encryption Standard, or DES, was the dominant encryption scheme in the world until the AES scheme was introduced in 2001. The DES was created in 1977 and uses 64-bit blocks with a 56-bit key. On the left side of the diagram below, the 64-bit plaintext goes through an initial permutation to produce the permuted input. The permuted input is then sent through 16 rounds of the same function that uses permutation and substitution. After the 16 rounds, the left and right halves of the current output are swapped to produce the preoutput. Finally, the preoutput is passed through a final permutation that is the opposite of the initial permutation to produce the ciphertext.
The 56-bit key is initially passed through a permutation function. For each of the 16 rounds, a 48-bit subkey is produced using a combination of a left circular shift and a permutation function, which is the same for each round. DES has the exact same structure as a Feistel cipher, except for the initial and final permutations. This means DES encryption and decryption can use the same functions.
Below is an explanation of DES using simplified DES. Simplified DES only uses 8 bits instead of 64 to make the process easier to walk through. Simplified DES is not used in the real world because it would be much easier to break.
The Avalanche Effect
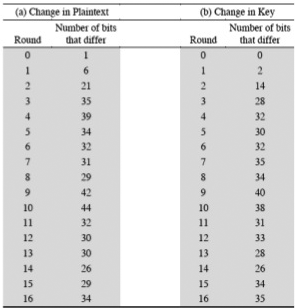
One of the beneficial properties of DES, and of any good encryption algorithm, is a small change in the plaintext or key produces a large change in the ciphertext. This is known as the avalanche effect. The table below shows how many bits are different in the plaintext and key during a run through of DES.
DES Weaknesses
One of the concerns about DES is the size of the key. With 56 bits, there are 256 possible keys. It would take thousands of years to break the cipher with a computer that could perform one DES encryption per microsecond. However, parallel computing has changed the game. Even in 1977 the creators of DES posited that the average time to break a DES cipher could be as little as ten hours with parallel computing. Today's typical PC configuration could break DES in about a year. Today's supercomputers could break it in an hour. A larger key size would help since DES with a key size of 128 bits would take over 100,000 years to break. However, DES was written with 56 bits, but there are alternatives to using DES.
Another potential weakness of DES is the substitution tables, or S-boxes that are used in the function rounds. The design of the DES algorithm has never been made public and some say that anyone with inside knowledge of the S-boxes would be able to cryptanalyze DES. No one has ever admitted to accomplishing this feat, however.
A timing attack is an attack that observes how long a given encryption or decryption takes. This exploits the fact that different inputs take different amounts of time to encrypt/decrypt. This has been shown to work to determine the number of bits equal to 1 of a DES key, but that still leaves 55 bits. It is unlikely that a timing attack would be able to crack DES or more sophisticated encryption algorithms.



