Computer Security :: Lessons :: Block Cipher Modes of Operation
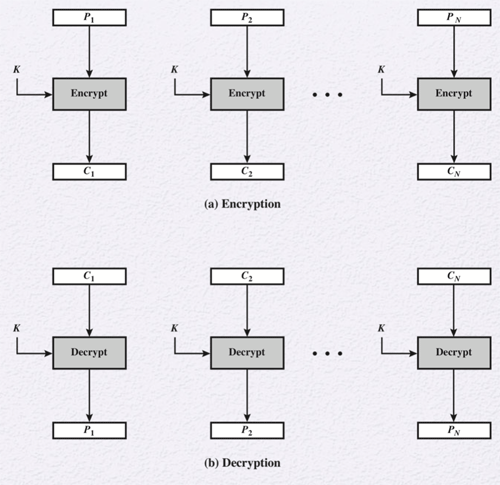
Electronic Codebook
Block ciphers encrypt plaintext and produce b-bit blocks of ciphertext. If the plaintext is larger than b, the block cipher breaks up the plaintext into multiple b-bit blocks. When the same key is used this leads to security issues since the ciphertext can be compared in an attempt to crack the encryption. For this reason modes of operation have been defined as techniques for enhancing an algorithm to increase its security.
A mode of operation can be evaluated based on the following properties:
- Overhead
- Error Recovery
- Error Propagation
- Diffusion
- Security
An electronic codebook (ECB) is the most basic mode of operation for enhancing block ciphers. Each block of plaintext is encoded independently using the same key. This is okay for secure transmission of single values, such as an encryption key, but this mode falls apart of lengthier messages. This is because there may be plaintext blocks that are the same, which would result in the same ciphertext. Watch the video below for more details.
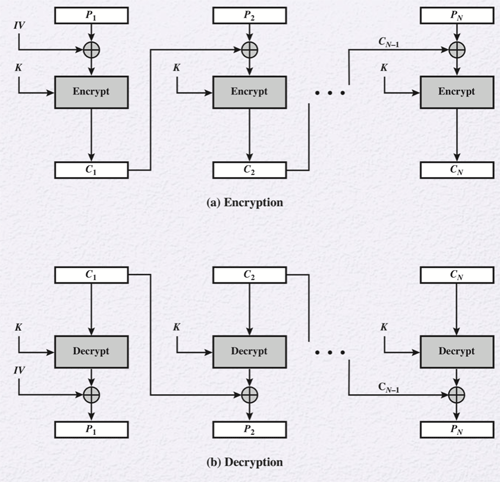
Cipher Block Chaining Mode
Cipher block chaining mode (CBC) produces different ciphertext blocks even with the same plaintext. This is because the input to the encryption algorithm is an XOR of the current plaintext and the previous ciphertext. Also, an initialization vector, or IV, is used to XOR the first block of plaintext. The IV should be protected just as a key is protected and should be unpredictable. One method of doing this is using a random data block generated by a random number generator. Another method is applying the encryption function to a nonce, which is a data block that will be unique to each encryption operation such as a counter, timestamp, or message number. CBC mode can be used for almost any type of block cipher operations.
Cipher Feedback Mode
Cipher feedback mode (CFB) converts a block cipher into a stream cipher, which means the message does not have to be padded to fit a specific block size and the encryption can operate in real time encrypting/decrypting characters as they are transmitted. While CFB mode works similar to a stream cipher, it is not a true stream cipher because the stream of bits depend on previous bits to perform encryption or decryption. CFB mode is a general-purpose stream-oriented cipher.
Output Feedback Mode
Output feedback mode (OFB) is similar to CFB, but the ciphertext is not used in the next round of encryption. An advantage of this mode is that errors do not propogate like they do in most other modes since the ciphertext is not used in the next round. It is easier for an attacker to modify portions of the ciphertext, however, to purposely change the recovered plaintext. OFB mode is useful for transmissions over noisy channels where errors may occur such as satellite communications.
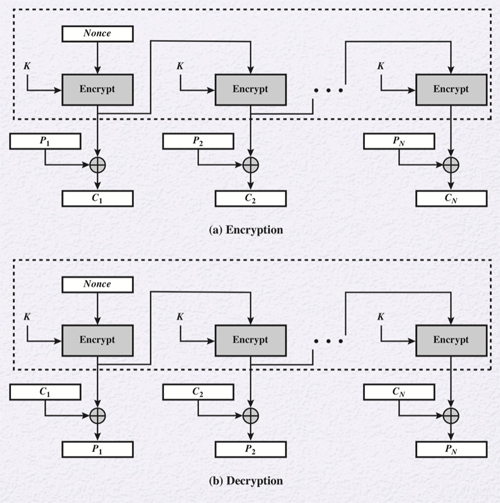
Counter Mode
Counter mode (CTR) is the fastest mode of operation. It uses a counter initially derived from a none in the encryption algorithm. The counter is the same size as the plaintext block and must be different for every block. Typically, the counter is just increased by one for every block. The result of the encryption is then XORed with the plaintext block to produce a ciphertext block. Blocks can be decrypted in parallel since nothing from a previous block affects the next block and any part of the plaintext can be encrypted or decrypted without going through the entire encryption/decryption process of the entire plaintext.
XTS-AES
A tweakable block cipher has three inputs: plaintext, a symmetric key, and a tweak that produce ciphertext. The tweak, unlike the key, does not need to be secret since it is only intended to add some variability. XTS-AES is a mode of operation meant to be used on sector-based devices such as hard drives. Instead of padding, XTS-AES uses ciphertext stealing where the last ciphertext block fills itself using ciphertext from the previous block. The video below explains the performance of XTS-AES, which should only be used for sector-based encryption.



