Computer Security :: Lessons :: AES
AES
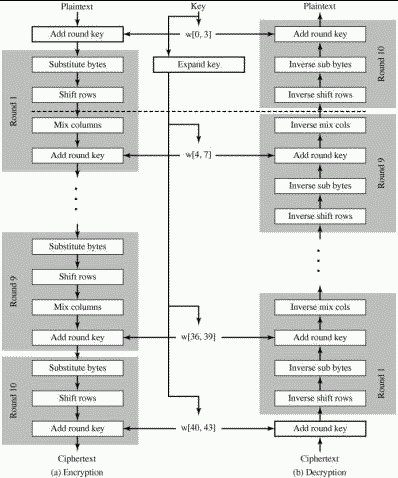
The Advanced Encryption Standard, or AES, was published in 2001 by the National Institute of Standards and Technology as a replacement for DES. While DES worked with 64 bits, AES has 128 (AES-128), 192 (AES-192), and 256 (AES-256) bit versions. As a symmetric block cipher, AES-128 copies 128 bits into a state array, which represents the 128 bits as a 4x4 matrix of bytes. The key length can be 16 bytes, 24 bytes, or 32 bytes depending on the number of bits in the plaintext. There are 10 function rounds for AES-128, 12 rounds for AES-192, and 14 rounds for AES-256. AES is more secure with a larger key size, but will take longer to execute. The AES algorithm makes heavy use of number theory and finite fields, but the math will not be covered by this lesson. If you are interested in the math behind AES check out this video.
AES Transformations
It is important to note that, unlike DES, AES is not a Feistel structure. In a Feistel structure half of the data block is used to modify the other half of the block before the two halves are swapped. AES processes the entire block of data at once using two substitutions, a permutation, and a bitwise operation.
- Substitution: A byte-by-byte substitution is performed on the block using a substitution table known as an S-box.
- ShiftRows: A permutation on the modified block.
- MixColumns: A substitution making heavy use of arithmetic.
- AddRoundKey: An XOR of the current block and a subkey is performed. This is the only portion of the round that uses any part of the key and is effectively a Vernam cipher.
AES Key Expansion Algorithm
The AES key expansion algorithm takes a four-word (16-byte) key as input and produces an array of 44 words (176 bytes). The key is copied into the first four words of an expanded key and the remainder of the expanded key is filled four words at a time. Most of the words are generated through a simple XOR, but every fourth word uses a more sophisticated algorithm that uses the following functions:
- RotWord: Performs a one-byte circular left shift on a word.
- SubWord: Performs a byte substitution on each byte of the input word using an S-box.
- Rcon: This is round constant value that is different depending on the round.
Below is a pseudocode version of the AES key expansion algorithm.
word KeyExpansion(byte key[16])
{
word w[44];
word temp;
for (i=0; i<4; i++)
w[i] = (key[4*1], key[4*i+1], key[4*i+2], key[4*i+3]);
for (i = 4; i < 44; i++)
{
temp = w[i - 1];
if (i % 4 == 0)
temp = SubWord(RotWord(temp)) ⊕ Rcon[i/4];
w[i] = w[i-4] ⊕ temp;
}
return w;
}



