Computer Security :: Lessons :: HMAC and CMAC
HMAC
The idea of using a hash function to generate a MAC is relatively new. HMAC or hash-based message authentication code was first defined and published in 1996 and is now used for IP security and SSL. The advantage of using a hash-based MAC as opposed to a MAC based a block cipher is speed. Hash functions like MD5 and SHA are generally faster in software than symmetric block ciphers like AES and DES.
A hash function cannot be used directly as a MAC since it does not rely on a secret key. The design objectives for an HMAC are the following:
- The ability to use available hash functions without modification.
- The ability to easily replace the embedded hash function in case faster or more secure functions become available.
- The ability to preserve the original performance of the hash function.
- The ability to use keys in a simple way.
- A well understood cryptographic analysis of the strength of the authentication mechanism.
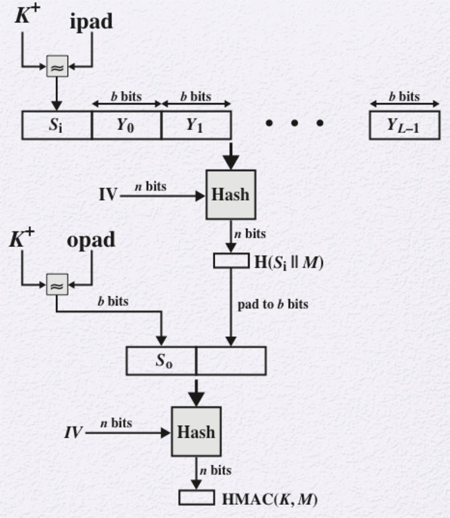
The diagram shows the general structure of HMAC using these terms:
- H: Embedded Hash Function
- IV: Initial Value Input
- M: Message Input
- Yi: ith block of M
- L = Number of Blocks in M
- b: Numbers of Bits in a Block
- n: Length of Hash Code Output
- K: Secret Key
- K+: K Padded with 0s
- ipad: 00110110 (36 in Hexadecimal) Repeated b/8 Times)
- opad: 01011100 (5C in Hexadecimal) Repeated b/8 Times)
The HMAC structure follows these steps:
- Append 0s to the left of K to create a b-bit string K+.
- XOR K+ with ipad to produce the b-bit block Si.
- Append M to Si.
- Apply H to the stream generated in the previous step.
- XOR K+ with opad to produce the b-bit block S0.
- Append the hash result from step 4 to S0.
- Apply H to the stream generated in step 6 and output the result.
CMAC
The Data Authentication Algorithm, or DAA, is a block cipher MAC based on DES. However, security weaknesses have led to its replacement. Cipher-based Message Authentication Code, or CMAC, is a block-cipher mode of operation for use with AES and 3DES. CMAC uses three keys: one key that is used for each step of the cipher block chaining and two keys that are the same length as the cipher block.



